Fingerprint identification - Is it as easy as it seems?
by Vicky Ang
23 Feb 2019
Fingerprint identification isn’t a phrase foreign to us. In fact, many of us use it, from our school attendance marking to unlocking phones. It is a common sight as a security feature, be it school computer labs or condominium houses. But have you ever wondered how it actually works?

What is fingerprint identification?
Fingerprint identification is a form of identification using the impressions made by the patterns found on the fingertips. No two people have similar fingerprints, and the patterns of any one individual’s fingerprint remain unchanged throughout life. Fingerprints offer a foolproof means of personal identification, because other personal characteristics may change, but fingerprints do not.
Some different kinds of fingerprint patterns include:
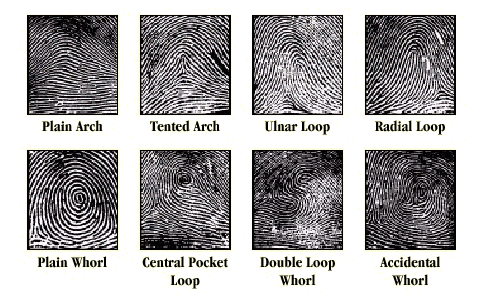
Look closely at your finger, you will be able to see one of these patterns on it!
Who discovered fingerprint identification?
In 1891, Juan Vucetich, an Argentine Police Official, began the first fingerprint files based on pattern types. In 1892, he made the first criminal fingerprint identification. He was able to identify a woman by the name of Rojas, who had murdered her two sons, and cut her own throat in an attempt to place blame on another. (For more concise information, visit the link below)
Some disadvantages?
For one, implementing a fingerprint system is costly and the scanners can’t distinguish between a exact detailed picture of a finger and the finger itself, leaving it open to trickery. In addition, if there are scars or injuries on your finger, the fingerprint will not be valid.
Other forms of identification?
Some include facial recognition, voice recognition, signature recognition, utilising DNA, retinal scanning and iris recognition.

Further Readings
If you want to find out more on fingerprint identification, feel free to visit some of this links: